Goal: Analyze and document the progression of APT28 Zebrocy Delphi loader/backdoor variants from 6.02 to 7.00.
#APT28/Sednit Zebrocy Implant
47a026d93ae8e0cc292e8d7a71ddc89e
similar to https://t.co/CU3ndKgnNu@DrunkBinary
as always submission by @clucianomartins and @CodexGigasSys ,Thanks— Rony (@r0ny_123) December 14, 2018
https://platform.twitter.com/widgets.js
Source:
Outline:
I. Background & Summary
II. Zebrocy Delphi Malware: Version 6.02
III. Zebrocy Delphi Malware: Version 7.00
IV. Zebrocy TForm1 Configurations
IV. Yara Signature
I. Background & Summary
APT28, also known as Sofacy, Fancy Bear, STRONTIUM, Pawn Storm, Sednit, continues to be very active lately targeting various government and political entities throughout 2018. Before diving deeper into the latest Zebrocy samples, I highly recommend reading ESET blog titled “Sednit: What’s going on with Zebrocy?” and Palo Alto Unit 42 one titled “Dear Joohn: The Sofacy Group’s Global Campaign.”
The Zebrocy Delphi variants serve as loaders and backdoors collecting victim information. They are occasionally UPX packed, store their configurations data in the resource section “RCData” as “TForm1” class. As a general rule, forms in Delphi are defined by the TForm class. The analyzed samples revealed malware version progression from 6.02 to 7.0 with the modified Timer objects and registry key and software information collection methods to scanning hosts for documents, archives, images, database, and configurations files.
Additionally, one of the oddities includes the hexadecimal art representation in Icon.Data object of TForm1.
The Python code obtains the resource as follows:
'''
Extract APT28 Zebrocy TForm1 Delphi Code from binary resource section
@VK_Intel
'''
import pefile
pe = pefile.PE("<PATH_TO_ZEBROCY")
# store our tform1_struct
tform1_struct = ""
offset = 0x0
size = 0x0
for rsrc in pe.DIRECTORY_ENTRY_RESOURCE.entries:
for entry in rsrc.directory.entries:
if entry.name is not None:
print(entry.name)
# search for TFORM1 resource
if entry.name.__str__() == "TFORM1":
offset = entry.directory.entries[0].data.struct.OffsetToData
size = entry.directory.entries[0].data.struct.Size
tform1_struct = pe.get_memory_mapped_image()[offset:offset+size]
print(tform1_struct)
The code output response is as follows:
DVCLAL
L30
LIBEAY32
PACKAGEINFO
PLATFORMTARGETS
SSLEAY32
TFORM1
MAINICON
b'TPF0\x06TForm1\x05Form1\x04Left\x02\x00\x03Top\x02\x00\x0cClientHeight\x03\x7f\x01\x0bClientWidth\x03\xc9\x01\x05Color\x07\tclBtnFace\x0cFont.Charset\x07\x0fDEFAULT_CHARSET...
Notably, the configuration contains all imported necessary SSL libraries LIBEAY32 and SSLEAY32, DVCLAL and L30 config, package info (contains Windows API utility code), and, most importantly, TForm1 Delphi main code.
The TForm1 resource is the main processor for the Window setting and creating objects TLabel, TEdit, and TMemo, which are descriptive of the malware functionality.
II. Zebrocy Delphi Malware: Version 6.0.2
For example, here is the code setting the Window and creating main victim collection and keylogger functionality and possible network domain parser module, taken from Zebrocy version 6.02
(0a6c1db916ac8ddf0ef67196279e12d163e07969d9cc68c0aed6b63d11f76d6c):
///////////////////////////////////////////////////
////// APT28 Zebrocy Malware TForm1 Class /////////
///////////////////////////////////////////////////
object Form1: TForm1
Left = 0
Top = 0
ClientHeight = 358
ClientWidth = 509
Color = clBtnFace
Font.Charset = DEFAULT_CHARSET
Font.Color = clWindowText
Font.Height = -11
Font.Name = 'Tahoma'
Font.Style = []
OldCreateOrder = False
PixelsPerInch = 96
TextHeight = 13
object c: TLabel
Left = 428
Top = 232
Width = 38
Height = 13
Caption = 'KEYLOG' // keylogger object
end
object Label2: TLabel
Left = 417
Top = 197
Width = 49
Height = 13
Caption = 'SYS_INFO' // machine system info object
end
object Memo3: TMemo
Left = 0
Top = 179
Width = 445
Height = 179 // network domain collector and parser object
Lines.Strings = (
'@ECHO OFF'
'FOR /F "tokens=1 delims=\ " %%n IN ('#39'net view^|FIND "\\"'#39') DO ('
' FOR /F "tokens=2 delims=[]" %%i IN ('#39'ping -a -n 1 -w 0 %%n^|FI' +
'ND "["'#39') DO ('
' ECHO %%i %%n>>1.txt'
' FOR /F "tokens=1,2,3,4 delims= " %%a IN ('#39'net view \\%%n^|FI' +
'ND " "'#39') DO ('
' IF "%%b"=="Disk" ('
' ECHO %%b: \\%%n\%%a>>1.txt'
' ) ELSE ('
' IF "%%b"=="Print" ECHO %%b: \\%%n\%%a>>1.t' +
'xt'
' )'
' )'
' )'
')')
TabOrder = 17
Visible = False
end
The malware drops a batch script to collect network domain information and saving it locally for exfiltration.
The observed TTimer timer objects (Enabled, OnTimer, Interval Parameters) code is as follows:
///////////////////////////////////////////////////
/// APT28 Zebrocy Malware Delphi Timer Class //////
///////////////////////////////////////////////////
object Timer_post: TTimer
Enabled = False
OnTimer = Timer_postTimer
Left = 144
end
object Timer_hello: TTimer
Enabled = False
Interval = 900000 // 900 seconds or 15 minutes interval
OnTimer = Timer_helloTimer
Left = 208
end
object Timer_scan: TTimer
Enabled = False
OnTimer = Timer_scanTimer
Left = 272
end
object Timer_all: TTimer
Enabled = False
Interval = 6000 // 6 seconds interval
OnTimer = Timer_allTimer
Left = 328
end
The all observed unique timer objects are as follows:
Timer_FirstTimer -> Interval 5000 miliseconds
Timer_handlTimer -> Interval 5000 miliseconds
Timer_SCRTimer -> Interval 60000 miliseconds
Timer_keyTimer -> Interval 120000 miliseconds
Timer_dsetTimer -> Interval 10000 miliseconds
Timer_mainTimer -> Interval 60000 miliseconds
Timer_allTimer -> Interval 6000 miliseconds
Timer_helloTimer -> Interval 900000 miliseconds
Timer_postTimer
Timer_scanTimer
Timer_lodsbTimer
Timer_downlTimer
Timer_regTimer
Timer_uplTimer
Timer_LogsTimer
Timer_DelTimer
Timer_SCRLDTimer
The POP3/SMTP mechanism is as follows:
///////////////////////////////////////////////////
/// APT28 Zebrocy Delphi SMTP/POP3/SSL Class //////
///////////////////////////////////////////////////
object IdPOP31: TIdPOP3
AutoLogin = True
SASLMechanisms =
Left = 272
Top = 112
end
object IdSMTP1: TIdSMTP
SASLMechanisms =
Left = 328
Top = 112
end
object IdSSLIOHandlerSocketOpenSSL1: TIdSSLIOHandlerSocketOpenSSL
MaxLineAction = maException
Port = 0
DefaultPort = 0
SSLOptions.Mode = sslmUnassigned
SSLOptions.VerifyMode = []
SSLOptions.VerifyDepth = 0
Left = 272
Top = 168
end
end
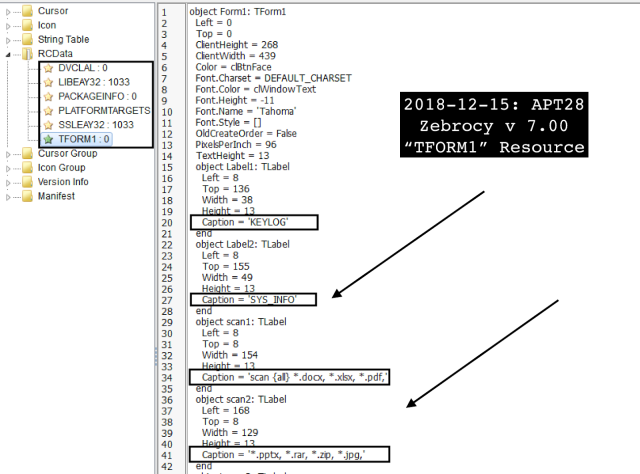
III. Zebrocy Delphi Malware: Version 7.00
Zebrocy Version 7.0
(SHA-256: 215f7c08c2e3ef5835c7ebc9a329b04b8d5215773b7ebfc9fd755d93451ce1ae):

The latest malware version includes the TLab scan object scanning for Microsoft Word, Microsoft Excel, Microsoft PowerPoint, PDF, archives (.rar, .zip) and image files (.jpg, bmp, tiff). Additionally, it also parses for configuration and database files (e.g,, .dat, .json, .db).
///////////////////////////////////////////////////
/// APT28 Zebrocy Delphi Special File Searcher ////
///////////////////////////////////////////////////
object scan1: TLabel
Left = 8
Top = 8
Width = 154
Height = 13
// Scanner for documents
Caption = 'scan {all} *.docx, *.xlsx, *.pdf,' // Scan for MS Word, Excel, PDF
end
object scan2: TLabel
Left = 168
Top = 8
Width = 129
Height = 13
// Scanner for documents, archives, & imagesCaption = '*.pptx, *.rar, *.zip, *.jpg,' // Scan for Powerpoint, archive, JPG imageendobject scan3: TLabel Left = 8 Top = 27 Width = 68 Height = 13 // Scanner for images Caption = '*.bmp, *.tiff /' // Scan for BMP and TIFF imageend... object Label3: TLabel Left = 8 Top = 46 Width = 147 Height = 13 // Scanner for configurations and database files Caption = 'scan {all} *.dat, *.json, *.db /' // Scan for .DAT, .JSON, .db end...

///////////////////////////////////////////////////
/// APT28 Zebrocy Delphi HKCU Registry Persistr ///
///////////////////////////////////////////////////
object Button2: TButton
Left = 309
Top = 3
Width = 122
Height = 25
Caption = 'HKCU\Environment'
TabOrder = 6
end
object Button3: TButton
Left = 310
Top = 34
Width = 122
Height = 25
Caption = 'UserInitMprLogonScript'
Tab
The all observed unique Timer objects are as follows (TTimer Timer Objects (Enabled, OnTimer, Interval parameters):
Timer_FirstTimer -> Interval 5000 miliseconds
Timer_taskTimer -> Interval 90000 miliseconds
Timer_sendTimer -> Interval 120000 miliseconds
Timer_SCRTimer -> Interval 120000 miliseconds
Timer_OTimer -> Interval 28800000 miliseconds
Timer_postTimer
Timer_mainTimer
The observed mail companies used for command-and-cotrol communications and exfiltration:
Leveraged Mail Servers:
ambcomission[.]com
seznam[.]cz
post[.]cz
india[.]com
Email Accounts:
tomasso25@ambcomission[.]com
kevin30@ambcomission[.]com
salah444@ambcomission[.]com
rishit333@ambcomission[.]com
karakos3232@seznam[.]cz
antony.miloshevich128@seznam[.]cz
b.huacop11@india[.]com
trasler22@ambcomission[.]com
trash023@ambcomission[.]com
IV. Zebrocy TForm1 Configurations
A. Zebrocy v6.02 TForm1 Config
(SHA-256: 0a6c1db916ac8ddf0ef67196279e12d163e07969d9cc68c0aed6b63d11f76d6c):
KEYLOG
SYS_INFO
@ECHO OFF
FOR /F "tokens=1 delims=\ " %%n IN ('net view^|FIND "\\"')
DO (M FOR /F "tokens=2 delims=[]" %%i IN ('ping -a -n 1 -w 0 %%n^|FIND "["')
DO ( ECHO %%i %%n>>1.txt S FOR /F "tokens=1,2,3,4 delims= " %%a IN ('net view \\%%n^|FIND " "')
DO ( IF "%%b"=="Disk" (0 ECHO %%b: \\%%n\%%a>>1.txt )
ELSE (IF "%%b"=="Print"
ECHO %%b: \\%%n\%%a>>1.txt ) ) ))
ddr3
*\Software\Microsoft\Windows\CurrentVersion
C:\Users\Public\dset.ini
ProductId
SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall
Software\Microsoft\Windows\CurrentVersion\Run
libeay32.dll
ssleay32.dll
p.bin
v6.02
GET_NETWORK
B. Zebrocy v7.00 TForm1 Config
(SHA-256: 215f7c08c2e3ef5835c7ebc9a329b04b8d5215773b7ebfc9fd755d93451ce1ae):
KEYLOG
SYS_INFO
!scan {all} *.docx, *.xlsx, *.pdf, *.pptx, *.rar, *.zip, *.jpg, *.bmp, *.tiff /
adr_for_scan
C:\Users\Public\officeexcp.bin
KLA
C:\Users\Public\kla.bin
scan {all} *.dat, *.json, *.db /
eg add
EG_EXPAND
eg delete
GET_NETWORK
HKCU\Environment\UserInitMprLogonScript
v7.00
libeay32.dll
ssleay32.dll
C. Zebrocy v7.00 TForm1 Config
(SHA-256: ae6326a8b0297dc6eff583f2305abaeab0347a3aef95fc51c5d76708cf32b73f)
SYS_INFO
eg add
EG_EXPAND
eg delete
C:\Users\Public\dset.ini
p.bin
v7.00
ssleay32.dll
libeay32.dll
C:\Users\Public\boot.ini
UserInitMprLogonScript
HKCU\Environment
One of the oddities related to the Zebrocy malware (SHA-256: ae6326a8b0297dc6eff583f2305abaeab0347a3aef95fc51c5d76708cf32b73f) includes Icon.Data {} object with the hexadecimal art.
V. Yara Signature
rule apt28_win32_zebrocy_loader {
meta:
author = "@VK_Intel"
reference = "Detects Zebrocy Component"
date = "2018-12-14"
strings:
$s1 = "Timer_postTimer" fullword wide ascii
$s2 = "Timer_mainTimer" fullword ascii wide
$s3 = "Timer_FirstTimer" fullword ascii wide
$s4 = "UserInitMprLogonScript" fullword ascii wide
$s5 = "KEYLOG" fullword ascii wide
$s6 = "SYS_INFO" fullword ascii wide
$s7 = "EG_EXPAND" fullword ascii wide
$s8 = "HKCU\\Environment" fullword ascii wide
$s9 = "C:\\Users\\Public\\" fullword ascii wide
$s10 = "scan {all}" fullword ascii wide
$r0 = "L30" fullword ascii wide
$r1 = "LIBEAY32" fullword ascii wide
$r2 = "TFORM1" fullword ascii wide
$r3 = "SSLEAY32" fullword ascii wide
$r4 = "DVCLAL" fullword ascii wide
$r5 = "PACKAGEINFO" fullword ascii wide
condition:
( uint16(0) == 0x5a4d and
( all of them )
or ( 3 of ($s*) and 2 of ($r*) ) or ( all of ($r*) and 2 of ($s*) ) )
}