Goal: Reverse and analyze Buhtrap Banking Trojan. This was one of the most high-profile Trojan attacking various financial institutions in Russia in 2015-2016.
Source: a6569546896b6d8ad95e4dbcc346a68b
Config Source: Github
Static Analysis: Buhtrap Trojan
I. === MZ Header ===
- signature: “MZ”
- reloc_table_offset: 64 0x40
- lfanew: 224 0xe0
II. === Packer / Compiler ===
- MS Visual C++ v8.0

III. === BINARY ===
# IMAGE_FILE_HEADER:
- Machine: 332 0x14c x86
- NumberOfSections: 4 4
- TimeDateStamp: “2016-09-06 11:23:33”
- PointerToSymbolTable: 0 0
- NumberOfSymbols: 0 0
- SizeOfOptionalHeader: 224 0xe0
- Characteristics: 259 0x103 RELOCS_STRIPPED, EXECUTABLE_IMAGE 32BIT_MACHINE
IV. === SECTIONS ===
NAME RVA VSZ RAW_SZ RAW_PTR nREL REL_PTR nLINE LINE_PTR FLAGS
- .text 1000 16f24 17000 400 0 0 0 0 60000020 R-X CODE
- .rdata 18000 80f2 8200 17400 0 0 0 0 40000040 R– IDATA
- .data 21000 190a8 10600 1f600 0 0 0 0 c0000040 RW- IDATA
- .rsrc 3b000 780 800 2fc00 0 0 0 0 40000040 R– IDATA
V. === SECURITY === Digital Certificate “Bit-Trejd” (Moscow, Russia)
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
54:46:0e:1f:cd:61:2c:d3:37:7a:c2:cd:76:e4:24:0f
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=GB, ST=Greater Manchester, L=Salford, O=COMODO CA Limited, CN=COMODO RSA Code Signing CA
Validity
Not Before: May 30 00:00:00 2016 GMT
Not After : May 30 23:59:59 2017 GMT
Subject: C=RU/postalCode=127051, ST=Moscow, L=Moscow/street=1st Kolobovskij pereulok d. 27/3 str.3 office 30, O=Bit-Trejd, OU=IT, CN=Bit-Trejd
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:b2:0a:6e:fb:0c:35:1a:7a:fe:01:ce:47:6f:90:
07:ba:4c:e4:c7:64:05:57:e1:19:21:e3:df:ef:c2:
60:7d:e0:1c:fa:9a:49:b3:d4:ad:8d:ba:59:e8:2a:
5d:6e:42:3e:4c:18:07:00:d4:50:60:09:c5:3b:62:
1e:e2:34:bd:be:1c:16:04:a5:37:6d:11:34:41:ad:
94:26:9a:80:d4:41:be:a1:1c:c8:19:d2:a7:0d:43:
d4:8e:15:b9:2d:1e:c9:26:57:49:b4:6b:2c:e5:34:
e2:7a:e8:9d:8c:16:0e:45:da:68:dd:97:f0:18:96:
34:f0:aa:fc:78:5d:18:95:39:6b:41:5b:6a:2b:cd:
20:30:1a:bf:3f:93:47:11:03:ed:3a:f4:c0:18:d8:
cb:cf:ba:9d:5f:5f:c2:d6:0d:3f:60:bd:d8:ca:0b:
bc:a2:b1:6b:2a:33:a5:af:ef:8e:90:be:67:16:13:
4e:58:01:48:dd:61:0e:85:11:f8:b0:83:d4:7a:40:
a3:50:ae:9e:a1:56:1a:a2:a1:a7:75:a1:04:9d:11:
60:42:f9:a7:9a:9f:cf:56:7a:c9:2b:00:66:39:98:
49:5a:7c:44:f1:62:d2:72:8b:e8:47:8f:46:5d:8e:
df:9c:2f:20:5e:e1:a7:ed:f0:60:f1:98:1e:4b:c6:
91:51
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Authority Key Identifier:
keyid:29:91:60:FF:8A:4D:FA:EB:F9:A6:6A:B8:CF:F9:E6:4B:BD:49:CE:12
X509v3 Subject Key Identifier:
54:4B:73:AE:F7:EA:10:02:52:02:6E:75:9A:6C:7A:B2:D8:70:42:16
X509v3 Key Usage: critical
Digital Signature
X509v3 Basic Constraints: critical
CA:FALSE
X509v3 Extended Key Usage:
Code Signing
Netscape Cert Type:
Object Signing
X509v3 Certificate Policies:
Policy: 1.3.6.1.4.1.6449.1.2.1.3.2
CPS: https://secure.comodo.net/CPS
X509v3 CRL Distribution Points:
Full Name:
URI:http://crl.comodoca.com/COMODORSACodeSigningCA.crl
Authority Information Access:
CA Issuers – URI:http://crt.comodoca.com/COMODORSACodeSigningCA.crt
OCSP – URI:http://ocsp.comodoca.com
=== RESOURCES ===
FILE_OFFSET CP LANG SIZE TYPE NAME
0x2fd88 1252 0x419 184 BITMAP #30994
0x2fe40 1252 0x419 324 BITMAP #30996
0x2ff84 1252 0 196 DIALOG DLG_INPUTQUERYSTR
0x30048 1252 0 440 DIALOG DLG_PRESETUP
0x30200 1252 0x243b 381 MANIFEST #1
=== SIGNATURE ===
——————————————–
000017d1 1299 classical random incrementer 0x343FD 0x269EC3 [32.le.8&]
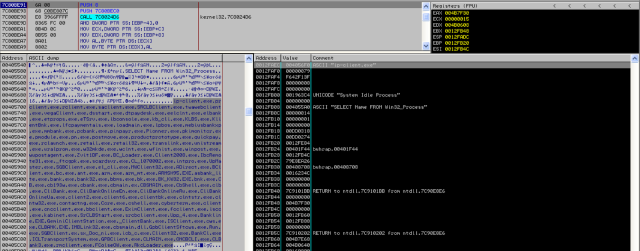
0001f410 2545 anti-debug: IsDebuggerPresent [..17]
00030380 3032 PADDINGXXPADDING [..16]
0003045a 917 SSH RSA id-sha1 OBJ.ID. oiw(14) secsig(3) algorithms(2) 26 [..15]
Configuration: Buhtrap Trojan
- Targeted processes:
p-client.exe.prclient.exe.rclient.exe.saclient.exe.SRCLBClient.exe.twawebclient.exe.vegaClient.exe.dsstart.exe.dtpaydesk.exe.eelclnt.exe.elbank.exe.etprops.exe.eTSrv.exe.ibconsole.exe.kb_cli.exe.KLBS.exe.KlientBnk.exe.lfcpaymentais.exe.loadmain.exe.lpbos.exe.mebiusbankxp.exe.mmbank.exe.pcbank.exe.pinpayr.exe.Pionner.exe.pkimonitor.exe.pmodule.exe.pn.exe.postmove.exe.productprototype.exe.quickpay.exe.rclaunch.exe.retail.exe.retail32.exe.translink.exe.unistream.exe.uralprom.exe.w32mkde.exe.wclnt.exe.wfinist.exe.winpost.exe.wupostagent.exe.Zvit1DF.exe.BC_Loader.exe.Client2008.exe.IbcRemote31.exe._ftcgpk.exe.scardsvr.exe.CL_1070002.exe.intpro.exe.UpMaster.exe.SGBClient.exe.el_cli.exe.MWClient32.exe.ADirect.exe.BClient.exe.bc.exe.ant.exe.arm.exe.arm_mt.exe.ARMSH95.EXE.asbank_lite.exe.bank.exe.bank32.exe.bbms.exe.bk.exe.BK_KW32.EXE.bnk.exe.CB.exe.cb193w.exe.cbank.exe.cbmain.ex.CBSMAIN.exe.CbShell.exe.clb.exe.CliBank.exe.CliBankOnlineEn.exe.CliBankOnlineRu.exe.CliBankOnlineUa.exe.client2.exe.client6.exe.clientbk.exe.clntstr.exe.clntw32.exe.contactng.exe.Core.exe.cshell.exe.cyberterm.exe.client.exe.cncclient.exe.bbclient.exe.EximClient.exe.fcclient.exe.iscc.exe.kabinet.exe.SrCLBStart.exe.srcbclient.exe.Upp_4.exe.Bankline.EXE.GeminiClientStation.exe._ClientBank.exe.ISClient.exe.cws.exe.CLBANK.EXE.IMBLink32.exe.cbsmain.dll.GpbClientSftcws.exe.Run.exe.SGBClient.ex.sx_Doc_ni.exe.icb_c.exe.Client32.exe.BankCl.exe.ICLTransportSystem.exe.GPBClient.exe.CLMAIN.exe.ONCBCLI.exe.CLBank3.exe.rmclient.exe.FColseOW.exe.RkcLoader.exe
- Targeted applications:
%PROFILE%…iBank2..%APPDATA%…%DESKTOP%…amicon,bifit,*bss,*ibank……..%PROGRAMFILES32%….%SYSTEMDRIVE%…*…*\……*gpb,inist,mdm,bifit,Aladdin,Amicon,*bss,Signal-COM,iBank2,*\bc.exe,*\*\intpro.exe,*cft,agava,*R-Style,*AKB Perm….*ELBA,*ELBRUS…%PROGRAMFILES64%….ቅ.*gpb,inist,mdm,bifit,Aladdin,Amicon,*bss,Signal-COM,iBank2,*\bc.exe,*\*\intpro.exe,*cft,agava,*R-Style,*AKB Perm
- Targeted visited websites:
SFT,*Agava,*Clnt,*CLUNION.0QT,*5NT,*BS,*ELBA,*Bank,ICB_C,*sped,*gpb……..*ICPortalSSL*.*isfront.priovtb.com*.*ISAPIgate.dll*.*bsi.dll*.*PortalSSL*.*IIS-Gate.dll*.*beta.mcb.ru*.*ibank*.*ibrs*.*iclient*.*e-plat.mdmbank.com*.*sberweb.zubsb.ru*. *ibc*.*elbrus*.*i elba*.*clbank.minbank.ru*.*chelindbank.ru/online/*.*uwagb*.*wwwbank*.*dbo*.*ib.*.
- Second-stage payload URL:
hxxp://rozhlas[.]site/news/business/release[.]bin (User Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT %u.%u;%s Trident/4.0)
-
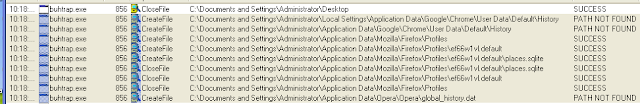
Parsed browser history
Google Chrome browser history location:
- %localappdata%\Google\Chrome\User Data\Default\History
- %appdata%\Google\Chrome\User Data\Default\History
Mozilla Firefox browser history location:
- %appdata%\Mozilla\Firefox\Profiles..*/*.GET…..*\places.sqlite
Opera browser history location:
- %appdata%\Opera\Opera\global_history.dat
- Internet search history queries: p.p1 {margin: 0.0px 0.0px 0.0px 0.0px; font: 12.0px Helvetica}
*SFT,*Agava,*Clnt,*CLUNION.0QT,*5NT,*BS,*ELBA,*Bank,ICB_C,*sped,*gpb……..*ICPortalSSL*.*isfront.priovtb.com*.*ISAPIgate.dll*.*bsi.dll*.*PortalSSL*.*IIS-Gate.dll*.*beta.mcb.ru*.*ibank*.*ibrs*.*iclient*.*e-plat.mdmbank.com*.*sberweb.zubsb.ru*. *ibc*.*elbrus*.*i-elba*.*clbank.minbank.ru*.*chelindbank.ru/online/*.*uwagb*.*wwwbank*.*dbo*.*ib.*
- Self-delete cmd script:
cmd.exe /C for /l %%x in (0,0,0) do (ping -n 3 127.0.0.1 > NUL & for %%p in (“%s”) do (del /f /q %%p & if not exist %%p exit))
p.p1 {margin: 0.0px 0.0px 0.0px 0.0px; font: 12.0px Helvetica}
p.p1 {margin: 0.0px 0.0px 0.0px 0.0px; font: 12.0px Helvetica} p.p1 {margin: 0.0px 0.0px 0.0px 0.0px; font: 12.0px Helvetica} p.p1 {margin: 0.0px 0.0px 0.0px 0.0px; font: 12.0px Helvetica} p.p1 {margin: 0.0px 0.0px 0.0px 0.0px; font: 12.0px Helvetica} p.p1 {margin: 0.0px 0.0px 0.0px 0.0px; font: 12.0px Helvetica} p.p1 {margin: 0.0px 0.0px 0.0px 0.0px; font: 12.0px Helvetica} p.p1 {margin: 0.0px 0.0px 0.0px 0.0px; font: 12.0px Helvetica} p.p1 {margin: 0.0px 0.0px 0.0px 0.0px; font: 12.0px Helvetica} p.p2 {margin: 0.0px 0.0px 0.0px 0.0px; font: 12.0px Helvetica; min-height: 14.0px}